Within a week of this post, millions of Americans will be introduced to AI technologies for the first time via big-budget Super Bowl advertisements. Millions of people who vote and participate in the economy will be forced to reckon with
My name is Matt Boegner. I'm an AI engineer and data architect based in Washington, DC
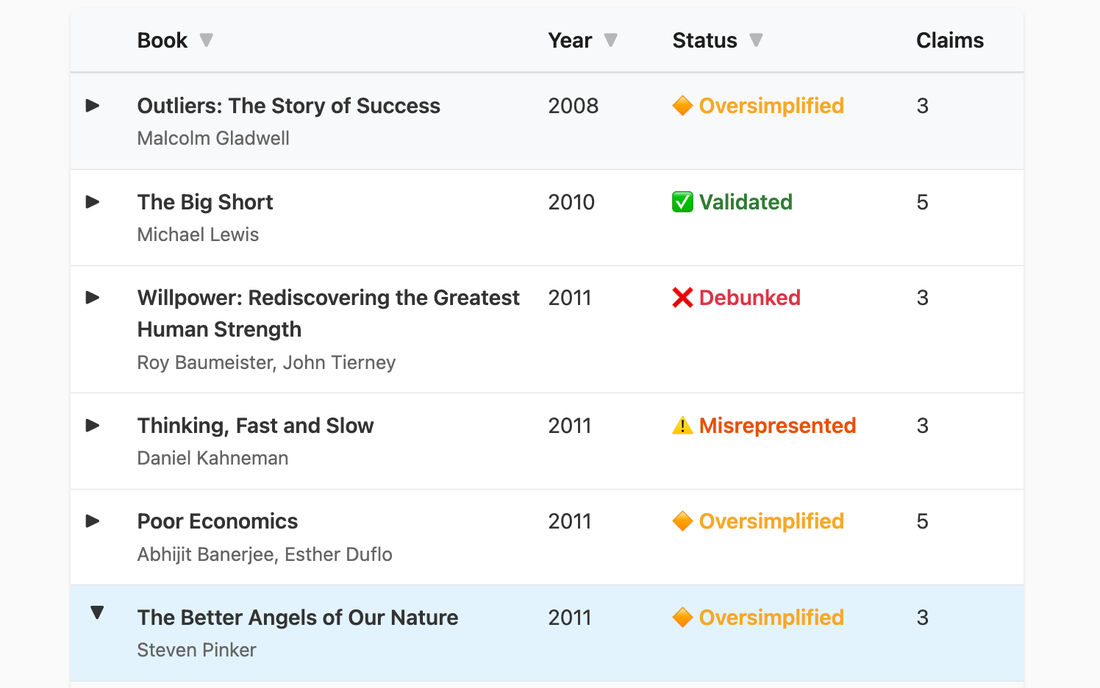
Who to Read on AI & Society (And Who to Ignore)
LLM Workflow Recommendations for Software Engineers - January 2025
This is art of a presentation I gave to my company on January 2nd, 2025. “What LLM should I use?” is more nuanced than it used to be. For coding or general technical tasks, I currently observe: * OpenAI o1/o1
AI Twitter Bookmarks - Q4 2022 - Non-Technical
I hope this semi-categorized list of links is a useful starting point for your exploration into the exciting advancements in AI!
Day 1 Experiments with StableDiffusion (AI Art - August 2022)
The folks over at Stability.ai [https://stability.ai/] released their text-to-image model into beta testing yesterday. Overall, I am extremely impressed! I look forward to following along and participating in the great community they're building over there.
Experiments with AI Art (August 2022)
I've been experimenting with AI-generated art for about 8 months now. I am consistently blown away by the pace of progress in the field and the creativity and ingenuity of the community. For your viewing pleasure, here is
AI Resources (May 2022)
I put together this post for the purpose of sharing interesting resources with friends and colleagues who want to learn more about advancements in the AI space. It's not meant to be comprehensive, but instead a branching out
Seven Data Engineering Trends to Watch in 2021
This is a repost of my feature on the Silectis blog [https://www.silect.is/blog/2020/1/5/improve-your-sql-skills-gaps-amp-islands-problems] . With our Magpie platform [https://www.silect.is/#data-lake-platform-section], you can build a trusted data lake in the cloud as
Improve Your SQL Skills: Master the Gaps & Islands Problem
Understanding how to solve the gaps and islands problem is critical for advanced SQL practitioners. In this post, we explore advanced techniques that can help you generate new insights and transform existing data into useful models.
Subscribe to Matt Boegner
Subscribe today and get access to a private newsletter and new content every week!